News & Insights
Defending industrial control systems: cybersecurity for operational technology (OT)
There are increasing cyberattacks on operational technology (OT). Here’s what manufacturers need to know about what makes their systems vulnerable and key considerations to protect their business.

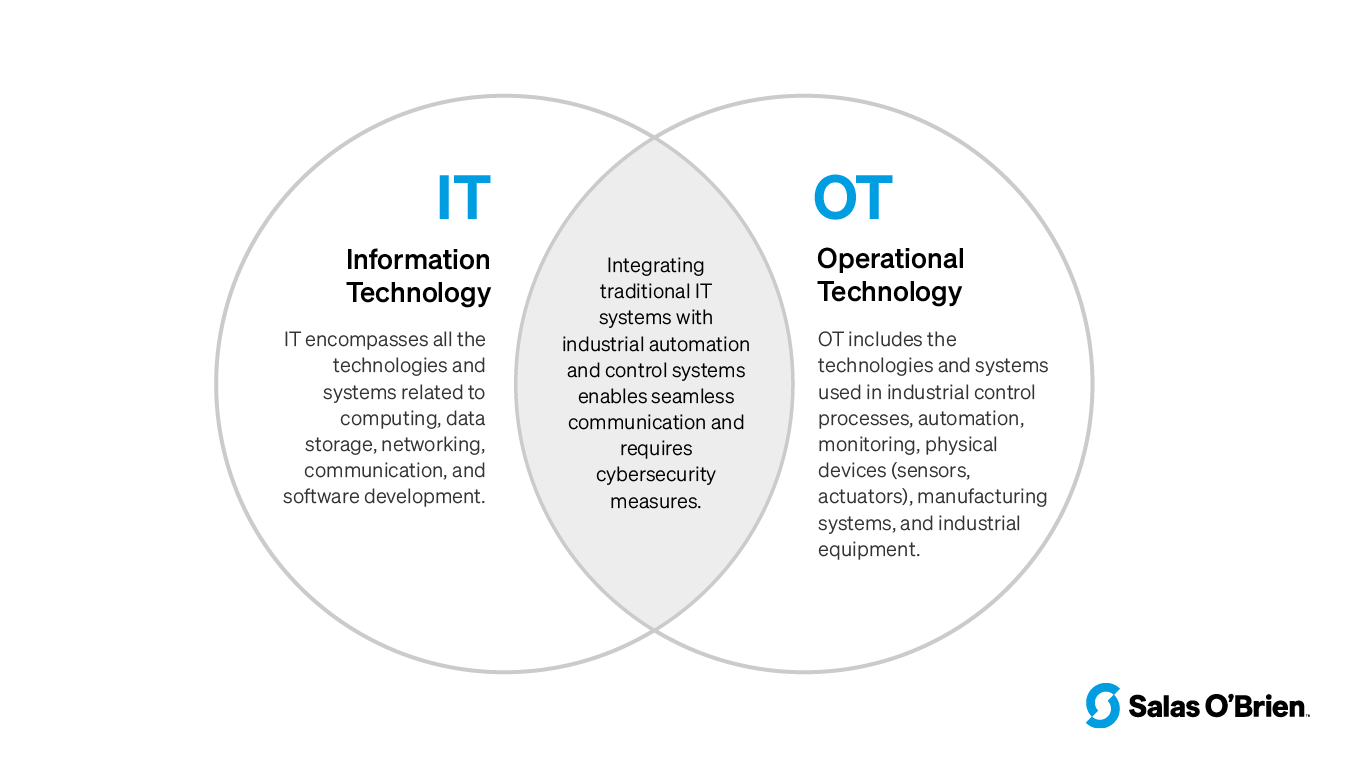
While cyberattacks on information technology (IT) cause damage to companies and organizations through data and communication disruption, attacks on operational technology (OT)—the hardware and software that controls and automates industrial equipment—can cause damage to physical systems in the real world. The consequences of OT cyberattacks can be far-reaching, leading to operational disruptions, financial losses, and even potential threats to public safety.
According to a report by McKinsey in 2021, approximately 90 percent of manufacturing organizations had experienced some form of cyberattack that impacted their production or energy supply. This statistic highlights the need for robust cybersecurity measures in safeguarding industrial control systems from malicious actors.
In this article, we will delve into the world of defending industrial control systems, focusing on the critical aspect of cybersecurity for operational technology. We will explore the emerging threat landscape, the unique challenges faced in securing OT, and best practices for implementing effective OT cybersecurity measures.
Complexity of cyber threats in operational technology
The convergence of IT and OT networks enables greater operational efficiency and flexibility. However, it has also exposed OT systems to new risks and vulnerabilities. The increasing number of interconnected devices and sensors in OT networks provides more entry points for cybercriminals to exploit. And because the systems are advancing so quickly, security can lag behind the advancements.
Here are the most common threats:
Advanced persistent threats (APTs) are sophisticated, long-term cyber threats typically orchestrated by well-resourced and highly skilled bad actors. In the realm of OT, APTs pose a significant risk as they employ stealthy techniques to gain persistent access to critical industrial control systems. By infiltrating OT networks, APT actors can conduct reconnaissance, steal sensitive information, and potentially disrupt or manipulate industrial processes, highlighting the need for advanced detection and defense mechanisms.
Ransomware attacks have seen a dramatic surge, and OT systems have become prime targets. These attacks typically involve the malicious encryption of critical OT data, rendering systems inoperable until a ransom is paid. The impact of successful ransomware attacks on OT can be severe, requiring organizations to implement robust backup strategies, resilient architectures, and proactive security measures to mitigate the risks posed by ransomware threats.
State-sponsored attacks on critical infrastructure, including OT systems, have grown in the realm of cybersecurity. Governments may target critical industrial infrastructure for various reasons, including gaining geopolitical advantages, sabotage, espionage, or strategic disruption.
Insider threats in OT environments encompass both malicious actions by disgruntled employees with access and unintentional actions by well-intentioned employees who fall victim to phishing attacks or by inadvertently misconfiguring systems, both of which can lead to security incidents. Organizations must implement strong access controls, comprehensive monitoring, and strong training programs to detect and mitigate both malicious and unintentional insider threats.
What makes operational technology vulnerable to cyberattacks?
In contrast to IT systems that primarily handle data and information flow, OT systems play a vital role in managing critical infrastructure. These systems, including supervisory control and data acquisition (SCADA), distributed control systems (DCS), and programmable logic controllers (PLCs), form the backbone of industrial operations, overseeing functions such as power grids and assembly lines.
Several factors contribute to the vulnerability of OT systems to cyberattacks:
Outdated OT systems: Many attacks target older devices running unpatched software and leverage techniques that are no longer effective against up-to-date IT networks. In addition, some devices have inherent vulnerabilities, such as backdoors and hardcoded passwords, which hinder updating and patching efforts and create potential entry points for attackers.
Targeted malware for OT: Over the past decade, there has been a significant development and deployment of malware specifically designed to target industrial control systems (ICS) and SCADA systems. The increase in attacks tailored for OT environments, with a particular focus on safety systems, highlights the growing threat landscape.
Interconnectivity of devices: The wide range of communication protocols used by devices like RFID, GPS trackers, security sensors, grid sensors, and condition sensors makes them susceptible to distributed denial-of-service (DDoS) attacks. These attacks can overwhelm devices by flooding them with a massive volume of communication, disrupting their functionality.
Risks associated with remote maintenance and third-party vendors: Remote maintenance solution providers and third-party vendors often have access to the assets they maintain, potentially introducing security risks. Organizations may have limited control over the security of the components connected to local production systems while they are connected to third-party vendors.
Lax security policies: There is a tension between ease-of-use and locking systems down. Often protocols are circumvented not with malicious intent, but simply by someone who needs to get things done. Cybersecurity for OT systems is sometimes overlooked because of tension between operators who need to keep things running and an IT group who doesn’t fully understand their needs. Security policies need to be designed in a way that keeps systems inherently secure without forcing work-arounds.
Key considerations for cybersecurity for operational technology
By understanding the risks and adopting proactive cybersecurity strategies, organizations can better protect their operational technology, preserve business continuity, and mitigate the potential physical and financial damage caused by OT cyberattacks.
Here are some key considerations for cybersecurity for OT:
1. Take a holistic approach that integrates OT and IT teams.
Tearing down silos to foster seamless communication between IT and OT teams gives you an edge in integrating people, processes, and technology. A collaborative approach can resolve the tensions between management who wants data, operators who keep things running, and IT professionals who secure the networks. Salas O’Brien can work with blended teams to develop comprehensive incident response plans that establish clear procedures for managing and recovering from cyberattacks and clear vendor management protocols to ensure OT equipment maintenance without compromising network security.
2. Implement advanced physical security systems to protect OT.
Utilize advanced access control technologies like biometric authentication, access cards, and security cameras to effectively monitor and manage access. Regularly review and update access privileges, promptly revoking access for individuals who no longer require it. Strategically position video cameras to act as deterrents and provide visual evidence in case of unauthorized access or tampering incidents.
In addition, intrusion detection systems (IDS) can identify unauthorized physical access attempts, tampering with cabling, or any suspicious activities within server rooms. IDS can trigger real-time alerts or initiate automated responses to swiftly mitigate potential threats. Salas O’Brien has an advanced physical security engineering team to help with this.
3. Leverage dashboarding and environmental monitoring.
Sophisticated environmental monitoring systems can track temperature, humidity, and other critical environmental parameters. Timely alerts and notifications can help prevent equipment failures caused by an OT cyberattack and mitigate risks associated with cooling system malfunctions. Holistic dashboards can monitor the performance of equipment, alerting teams quickly to any changes in performance. Salas O’Brien can work with your team to design and implement these systems.
4. Invest in redundant power.
Redundant power supply systems can ensure uninterrupted operation of servers during power outages or attacks on power infrastructure. Uninterruptible Power Supply (UPS) systems and backup generators can provide emergency power, maintaining server availability and preventing disruptions. Salas O’Brien can design power systems at small and large scales to create resilience.
5. Deploy a robust employee training and awareness program.
Regularly conduct comprehensive training programs to educate employees on best practices. Foster a culture of security consciousness for OT as well as IT systems so your team feels secure standing up for protocols even when circumventing them creates convenience. Training should cover topics to minimize human vulnerabilities that attackers exploit. Salas O’Brien can consult on systems and training for this.
6. Conduct regular audits and invest in continuous commissioning services.
Regular audits and thorough security assessments can identify vulnerabilities and weaknesses to close security gaps in industrial systems before they become a problem. Continuous commissioning can make this a regular part of maintaining the security of your industrial systems by alerting your team so they can quickly respond. Salas O’Brien can help with security assessments and continuous commissioning to keep your systems safe.
Salas O’Brien has the breadth and depth to offer industrial cybersecurity holistic solutions from assessment to design, implementation, and monitoring. Want to talk about cybersecurity for your operational technologies? Reach out to [email protected]
For media inquiries on this article, reach out to Stacy Lake.

Solutions in Industrial Cybersecurity
While cyberattacks on information technology (IT) cause damage to companies and organizations through data and communication disruption, attacks on operational technologies (OT) cause damage to physical systems in the real world.
Our report covers:
- What makes OT vulnerable to cyberattacks.
- Security audits and vulnerability assessments
- Zero trust architecture frameworks
- Firewall applications and endpoint security

Dave Jennings, PE, CISA
Dave Jennings is an industrial cybersecurity consultant who works closely with clients to improve and innovate their industrial controls systems (ICS). His main optimization areas of focus are: SCADA controls and visualization, ICS networking, cybersecurity, and data collection and reporting. Dave provides consulting and audits. He serves as an Associate Vice President at Salas O’Brien. Contact him at [email protected].

John Glenski, CPM
John Glenski is a leader in digital transformation in the industrial sector with a demonstrated history of providing data-driven outcomes for the world’s largest manufacturers. John works collaboratively with internal and external partners to deliver innovative solutions for smart manufacturing (automation, material handling, and data/information solutions) with a focus on sustainable applications. John serves as a Principal, Automation & Digital Solutions at Salas O’Brien. Contact him at [email protected].



