News & Insights
Mitigating risk in the new normal: physical security solutions and threat assessment
Adapting to evolving threats, clients are seeking physical security solutions and expert threat assessment for relevant and effective risk management strategies.

New physical security threats are emerging every day. Businesses, campuses, public venues, and municipalities are compelled to develop robust risk management strategies and implement effective physical security measures in order to adjust to the ever-changing “new normal.”
This article delves into the changing security landscape; examines how physical security designers approach the concept of threats; looks at the human factor in physical security; explores technological advancements; and highlights essential considerations for building owners.
The evolving physical security landscape and its impact on organizations
Once considered an add-on to building design, physical security is now seen as an integral part of the overall architectural concept. This shift reflects the growing recognition that security measures should seamlessly blend into the building’s fabric. Measures like hardening the perimeter through fences, bollards, and landscapes; implementing secure vestibules; or establishing single points of entry are examples of architectural solutions that pair with technology to create a comprehensive physical security approach.
While traditional risks like burglaries and vandalism persist, they are now accompanied by more sophisticated challenges, such as terror attacks or active shooter incidents. Some of the most significant shifts in physical security have occurred in existing buildings such as schools and churches, largely due to the escalation of violent events. Many of these buildings were not initially designed with security in mind, making effective renovation strategies crucial to meet current protection needs.

How physical security designers think about threats
The role of physical security design is to effectively delay and reduce the potential impact of security incidents. This objective is at the heart of security technology. Once the necessary devices are in place and operational, they enable early detection of any changes in the physical environment, providing security professionals with valuable reaction time. Video surveillance, access control systems, and intrusion detection can, for instance, swiftly identify activities such as fence jumping, car break-ins, or tampering with doors.
Security designers adopt a concentric circles approach and consider multiple layers of security. Starting from the perimeter, security measures are implemented in successive rings, extending inward to areas like lobbies, employee-only zones, and even highly secure spaces housing sensitive files or valuable assets. Access control is also implemented in layers, whether as simple as card entry or more advanced like biometrics.
Risk mitigation strategies are about working out the scenarios in a tabletop exercise where threats are weighed by likelihood and impact, then responded to through strategy and design. These types of exercises are never one-and-done. They have to be revisited regularly to keep security measures effective and relevant as the environment changes.

The human factor in physical security
Often when security measures fail, there is a human factor. The challenge is that the friction security measures create to protect us is usually inconvenient. People frequently find ways to bypass security systems by propping open doors for easier personal access, leaving windows open for fresh air, or allowing unauthorized individuals to enter via tailgating onto a property.
Security measures can also conflict with what we consider polite behavior. Being friendly and holding the door for someone or letting them in without a proper badge may seem nice, but it can allow unauthorized access.
Awareness programs are often just as important as the security technology itself, not only for what is in place and why, but also for how to react when the security systems are tripped. By emphasizing both the importance of security technology and the appropriate actions to take during security incidents, organizations can enhance overall security effectiveness.

Advances: where is physical security technology going?
Security technology is evolving to keep pace with the threats. Here is what our experts are seeing:
Better video at lower costs
Did you ever see a detective show where someone pointed to a grainy screen and said to their partner, “Enhance that”? The quality of video surveillance cameras has jumped dramatically in the past 10 years. High-resolution cameras with dynamic range used to be expensive, but now dealing with varying light levels is a feature that is much more affordable. Video codecs are also becoming more efficient, requiring less bandwidth while providing more efficient storage, empowering facilities to upgrade without major infrastructure changes.
More use of ballistic glass
Many clients are opting for large glass walls with ballistic-rated glass and plastic laminates to prevent the glass from shattering and leaving the frame if someone were to fire a gun at it. The goal is to ensure that the glass remains intact to contain a threat and prevent intrusion. But ballistic glass can be expensive. The factors driving the cost include the type of material, level of protection, and the size of the glass.
Mobile apps and cloud-based solutions
Security personnel were once confined to a bank of monitors in a control room, but mobile apps with cloud-based storage now facilitate conducting rounds while staying connected to camera views and notifications. The integration of mobile technology is empowering personnel with real-time access and mobility for efficient surveillance and incident response from anywhere.
Cameras with video analytics
Many manufacturers are creating cameras that are smart enough to process what they are seeing. They support security personnel by alerting them when something unusual happens. For example, they can flag footage when something is moved from an area or into an area. They can also spot a car moving the wrong way.
Physical security information management (PSIM)
PSIM is a specialized software category that integrates different security applications. Internal communications facilitate seamless switching between systems, replacing the old hard-wired and relay methods. One application for this type of product is connecting different sites to a single platform. For example, a school district with multiple schools could consolidate communications and increase collaboration between campuses. This integration is not off-the-shelf; instead, it involves unique systems that collaborate and work together, ultimately making operations more streamlined and user-friendly.
Artificial intelligence (AI)
The use of AI is emerging in physical security. Facial recognition is just one aspect of what’s possible. AI can analyze and process vast amounts of security-related data, such as video footage, access logs, and sensor data, to identify patterns and extract valuable insights. This capability enables security teams to optimize security protocols, enhance overall effectiveness, and make informed decisions. Additionally, AI is evolving to assist security personnel by utilizing predictive analysis to help direct attention to potential threats and areas of concern.
Cybersecurity for physical security data
Physical security systems can generate a lot of sensitive data that has to be kept safe. The best practice is to use established equipment brands with good protocols so that whatever you capture can be safely encrypted and stored.
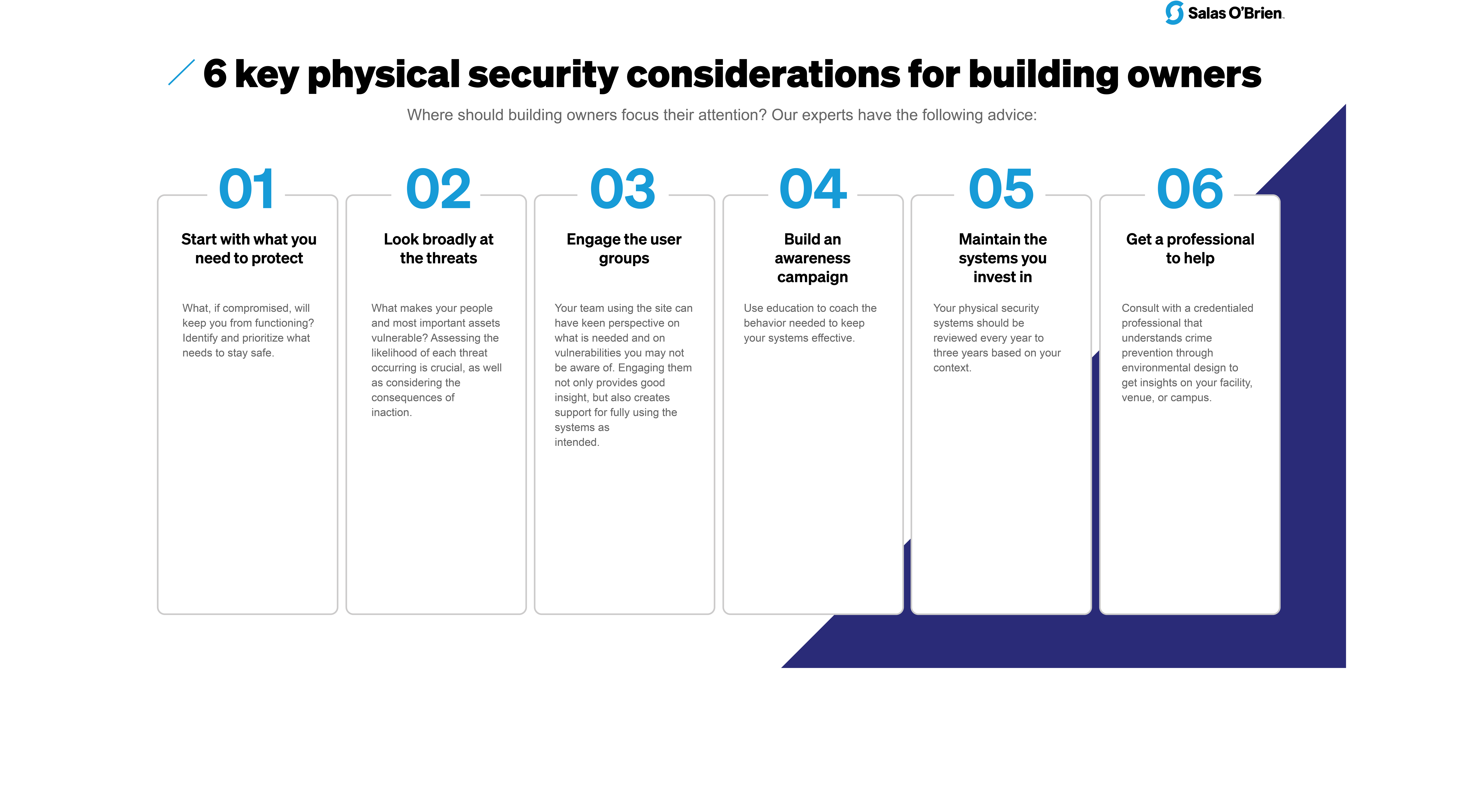
6 key physical security considerations for building owners
Where should building owners focus their attention? Our experts have the following advice:
- Start with what you need to protect. What, if compromised, will keep you from functioning? Identify and prioritize what needs to stay safe.
- Look broadly at the threats. What makes your people and most important assets vulnerable? Assessing the likelihood of each threat occurring is crucial, as well as considering the consequences of inaction.
- Engage the user groups. Your team using the site can have keen perspective on what is needed and on vulnerabilities you may not be aware of. Engaging them not only provides good insight, but also creates support for fully using the systems as intended.
- Build an awareness campaign. Use education to coach the behavior needed to keep your systems effective.
- Maintain the systems you invest in. Your physical security systems should be reviewed every year to three years based on your context.
- Get a professional to help. Consult with a credentialed professional that understands crime prevention through environmental design to get insights on your facility, venue, or campus.
Salas O’Brien is helping clients navigate the changing security landscape with physical security solutions and expert threat assessment. We help businesses identify and mitigate potential risks; protect their people, assets, and operations; and stay ahead of the curve in today’s rapidly evolving security environment.
For media inquiries on this article, reach out to Stacy Lake.

Rick Lavin, PSP, LEED AP
Rick Lavin is a physical security systems designer with over 25 years’ experience who specializes in complex, high-capacity public venues. His years spent working in spaces where thousands of people gather has given him a unique perspective on security needs and risk assessment. He has led design for stadiums and arenas, entertainment venues, university projects, and municipal buildings. Rick serves as a Senior Consultant for Salas O’Brien. Contact him at [email protected].

Ben Levison, MBA, CPP
Ben Levison has more than 30 years of security industry experience. He is an accomplished security professional with expertise in security operations, security technologies, site assessments, financial management, contracted services, crisis management, and program development. Throughout his career, Ben has been involved with developing global security “Best Practices” for Fortune 500 companies; managed regional executive protection, event security, and intellectual property programs; and developed service protocols and conducted audits to measure operational effectiveness. Ben serves as a Senior Security Consultant for Salas O’Brien. Contact him at [email protected].

Ann Paul
Ann Paul is an accomplished security system designer with a passion for driving innovation in the built environment. With a strong background in project management, she excels in working with cross-functional teams to deliver exceptional results in protecting her clients. Ann serves as a Consultant for Salas O’Brien. Contact her at [email protected].